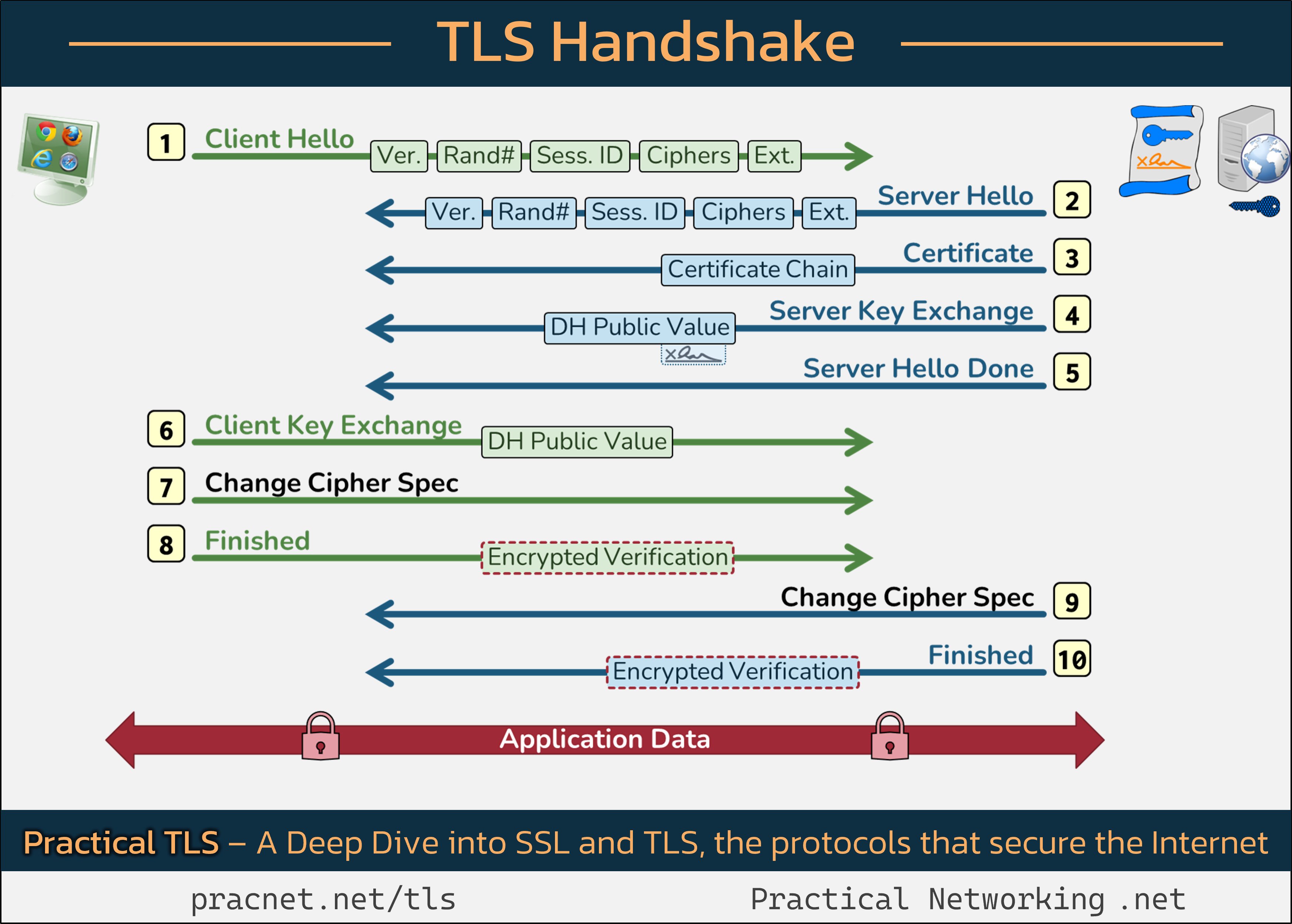
Understanding the TLS Handshake: Uncovering the Secrets Behind That Secure Padlock 🔒
In today’s digital landscape, ensuring a secure connection between your device and a website is critical. This post will take you through the TLS handshake process, illuminating everything that occurs to secure your browsing experience and earn that reassuring padlock icon in your browser’s address bar.
To help visualize this complex interplay, I’ve referenced an informative infographic. I recommend opening it in a new tab for a better understanding as we delve into the details.
Exploring the Basics
Before we jump into the handshake itself, it’s essential to understand that the primary objectives of SSL/TLS are:
- ✅ To authenticate the server’s identity.
- ✅ To establish secure session keys for data protection.
As we explore each stage of the handshake, keep in mind that the exchanges involve “Records”, which differ from conventional “Packets”. A single record can span multiple packets, and vice versa.
Additionally, familiarity with basic cryptographic concepts such as Hashing, MACs and HMACs, and Encryption will enhance your understanding. If you’re new to these concepts, I’ve included helpful video links.
Now, let’s break down the process of the TLS handshake step-by-step.
Step 1: Client Hello
The TLS handshake begins with the Client—your web browser—sending a Client Hello message that includes five crucial fields:
- SSL Version
- Random Number
- Session ID
- Cipher Suites
- Extensions
These components play distinct roles in achieving the handshake’s key objectives.
1.1 SSL Version
The Client announces the highest SSL version it supports, such as SSL 3.0, TLS 1.0, or more current versions like TLS 1.2 and TLS 1.3. The server responds with its compatible SSL version, and both parties agree on the most secure option.
1.2 Random Number
The Client generates a 32-byte random value, which will contribute entropy to the session keys, bolstering the security of the exchanged data.
1.3 Session ID
This feature allows for “Session Resumption,” meaning the Client and server can reconnect using previous handshake information instead of
Share this content: