Understanding the TLS Handshake: Unlocking the Secrets Behind Your Padlock 🔒
When you browse the web and see that reassuring padlock icon, have you ever wondered what’s going on behind the scenes? The process that secures your connection to websites is known as the TLS Handshake. In this post, we’ll explore every step that occurs during this critical interaction between your device and the website you’re accessing, all aimed at achieving that coveted padlock.
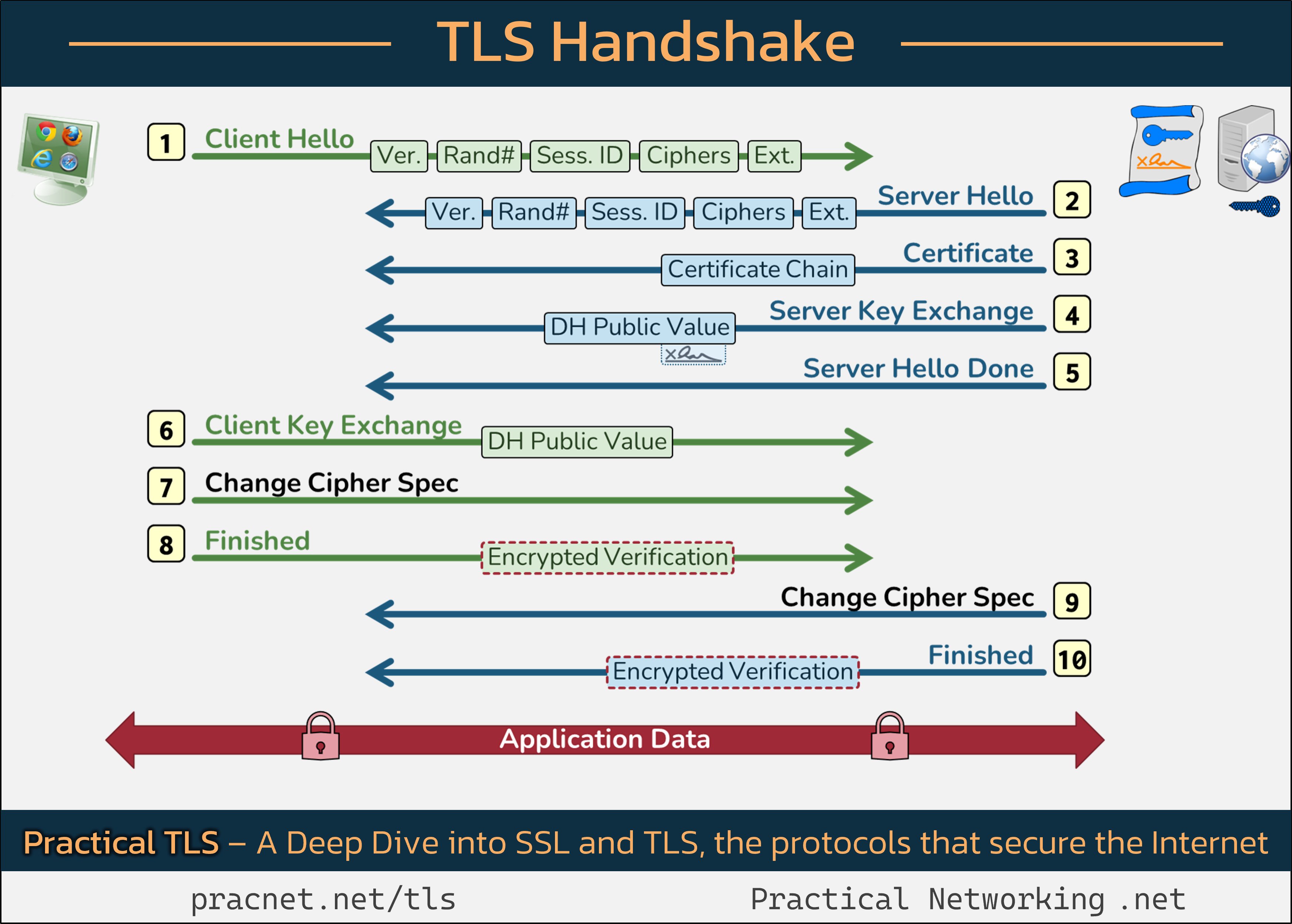
It might be useful to have this infographic open in a separate tab as you read through the explanations.
Introduction to TLS
Before diving into the specifics of the handshake process, let’s clarify the two main objectives of SSL/TLS:
- Authentication: Ensuring the server is indeed who it claims to be.
- Session Key Establishment: Creating session keys to encrypt the data exchange.
Key Concepts to Understand
Before we get into the hands-on details of the TLS handshake, it’s essential to distinguish between two crucial concepts:
-
Records vs. Packets: In the handshake, the message exchanges are termed “Records,” which can differ from “Packets.” Multiple Records might fit into a single Packet, and conversely, one Record might be spread across several Packets.
-
Cryptography: A basic familiarity with cryptographic concepts such as Hashing, MACs, and Encryption will enhance your understanding of how TLS operates. However, we won’t delve into these topics in detail here. For those interested, resources are readily available online.
With these foundational elements clarified, let’s move on to breaking down the steps of the TLS Handshake.
Step 1: Client Hello
The TLS handshake commences with the client (your web browser) sending a Client Hello message. This message encompasses five crucial pieces of information:
- SSL Version
- Random Number
- Session ID
- Cipher Suites
- Extensions
Each field plays a significant role in setting the stage for a secure connection.
Detailed Insights:
- SSL Version: The Client communicates the highest SSL version it supports (e.g., SSL 3.0, TLS 1.2). The Server responds with its own highest version, and they
Share this content:




Thank you for sharing this comprehensive overview of the TLS handshake process! If you’re experiencing issues with HTTPS connections or the padlock icon not appearing despite properly configured certificates, there are a few troubleshooting steps you can try: