Understanding the TLS Handshake: Unlocking the Secrets Behind That Padlock 🔒
When you visit a website, have you ever wondered how your information is secured and why that reassuring padlock appears in your browser? In this article, we’ll delve into the intricacies of the Transport Layer Security (TLS) handshake, which is a crucial process in establishing a secure connection between your web browser and the websites you visit.
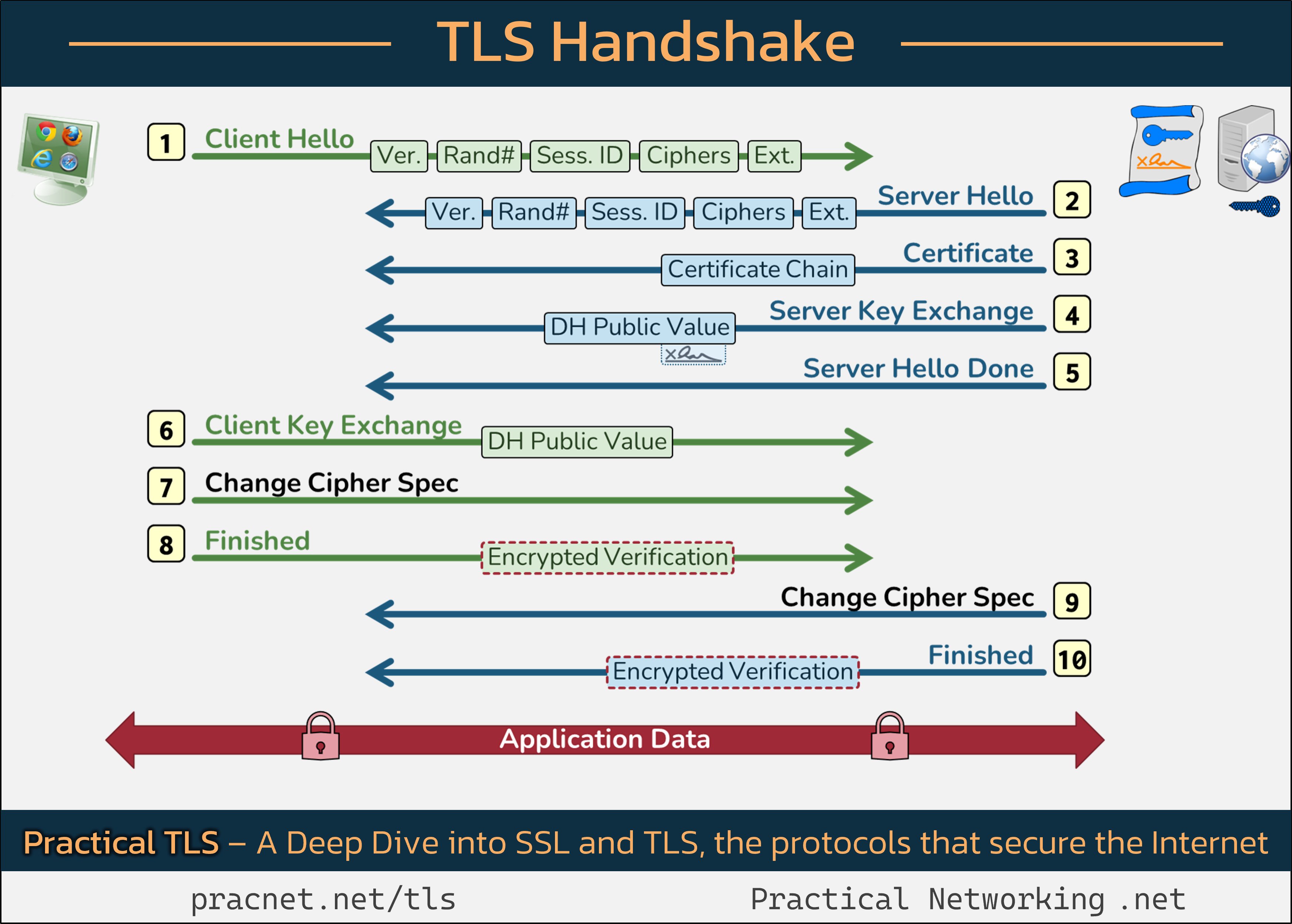
To enhance our discussion, I’ll reference an informative infographic that outlines the communication between your browser (the client) and the server hosting the website. You might find it helpful to keep this image handy as we navigate through the handshake process.
The Purpose of SSL/TLS
Before diving into the handshake itself, it’s essential to understand that the primary objectives of SSL/TLS are twofold:
- Authentication: Ensuring that the server is indeed the entity it claims to be.
- Data Integrity: Establishing session keys to secure the data transmitted between the client and server.
A Quick Note on Terminology
It’s important to distinguish between “records” and “packets.” Each line in the provided infographic represents a record in the TLS handshake, which differs from packets. A single packet may contain multiple records, or conversely, multiple packets might be needed to transmit a single record.
Additionally, familiarizing yourself with some cryptographic concepts such as hashing, MACs (Message Authentication Codes), and encryption will significantly enrich your understanding of the TLS handshake. Although we won’t explore these concepts deeply here, I recommend researching them for better context.
The Steps of the TLS Handshake
1️⃣ Client Hello
The TLS handshake begins with the client sending a Client Hello message. This message contains five key components:
- SSL Version
- Random Number
- Session ID
- Cipher Suites
- Extensions
Each of these fields plays a significant role in the handshake process.
1️⃣.1 SSL Version
The client specifies the highest SSL/TLS version it supports. In return, the server will offer its highest supported version, and the two will agree on the most secure mutual version available.
1️⃣.2 Random Number
The client generates a 32-byte random number, which will contribute to creating session
Share this content:




Thank you for sharing this detailed overview of the TLS handshake process. Understanding this sequence is crucial for diagnosing SSL/TLS-related issues on your website. If you’re experiencing connectivity problems or SSL errors, here are some troubleshooting steps you can try: