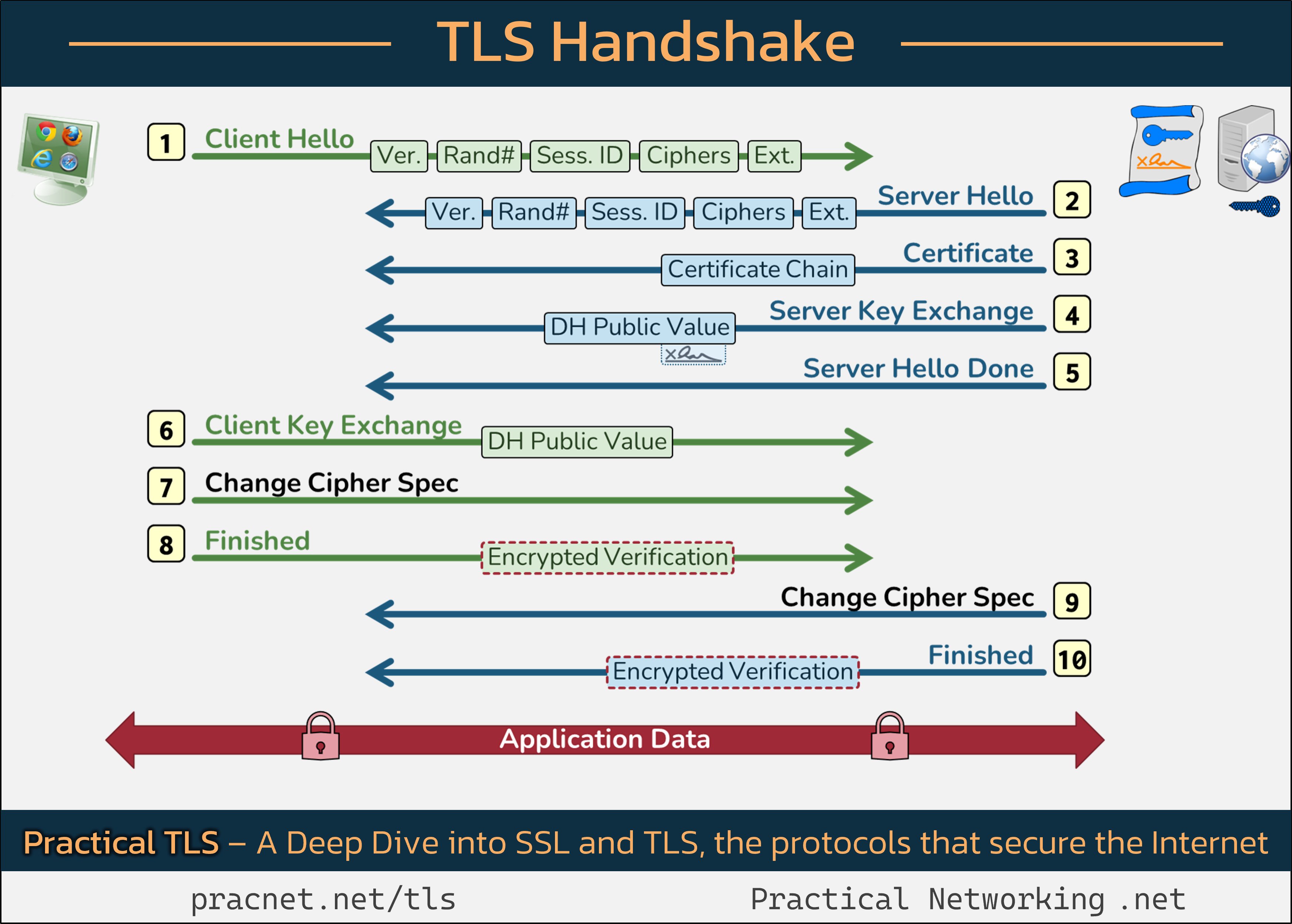
Understanding the TLS Handshake: The Journey to the Coveted Padlock 🔒
In today’s digital age, the security of our online interactions has never been more important. One of the primary milestones that indicates a secure connection is the appearance of the padlock icon next to your website’s URL. But how does this secure connection come about? In this blog, we’ll break down the intricate process known as the TLS handshake, illustrating everything that happens between your browser and the web server to establish that precious secure connection.
To enhance your understanding, keep this infographic handy as we explore the handshake process:
The Objective of TLS
Before diving into the handshake details, it’s crucial to understand the two primary objectives of TLS:
- ✅ Authentication: Ensuring the server is genuinely who it claims to be.
- ✅ Confidentiality: Establishing session keys that will safeguard the data transferred.
But before we dissect the handshake, let’s clarify two key concepts.
Distinction Between Records and Packets
In the infographic, each line represents a “Record” in the TLS handshake. It’s important to note that a Record is not synonymous with a Packet. A single Packet can carry multiple Records at once, or it may require multiple Packets to transport a single Record.
Fundamental Cryptographic Concepts
A basic understanding of certain cryptographic principles will enhance your grasp of the TLS handshake:
- Hashing – Essential for data integrity.
- MACs and HMACs – Used for ensuring authenticity.
- Encryption – For maintaining data confidentiality.
These concepts will be touched on lightly, as we focus primarily on the handshake process.
The TLS Handshake Process
1️⃣ Client Hello
The handshake begins with the “Client Hello,” where your web browser communicates its capabilities to the server. This message contains five crucial fields:
- SSL Version: Indicates the highest version of SSL/TLS supported by the client (e.g., TLS 1.2 or TLS 1.3).
- Random Number: A 32-byte random number generated by the client to provide entropy for session keys.
- Session ID: Used for potential session resumption.
- Cipher Suites: A list of encryption methods supported by the client.
- Extensions
Share this content: