
Greetings, cybersecurity enthusiasts! I’m the reporter who covered SentinelOne’s industry sidelining, and I could really use your support.
Title: Seeking Insights on Industry Silence: A Call for Perspectives Hello, cybersecurity community, I’m Raphael Satter, one of...
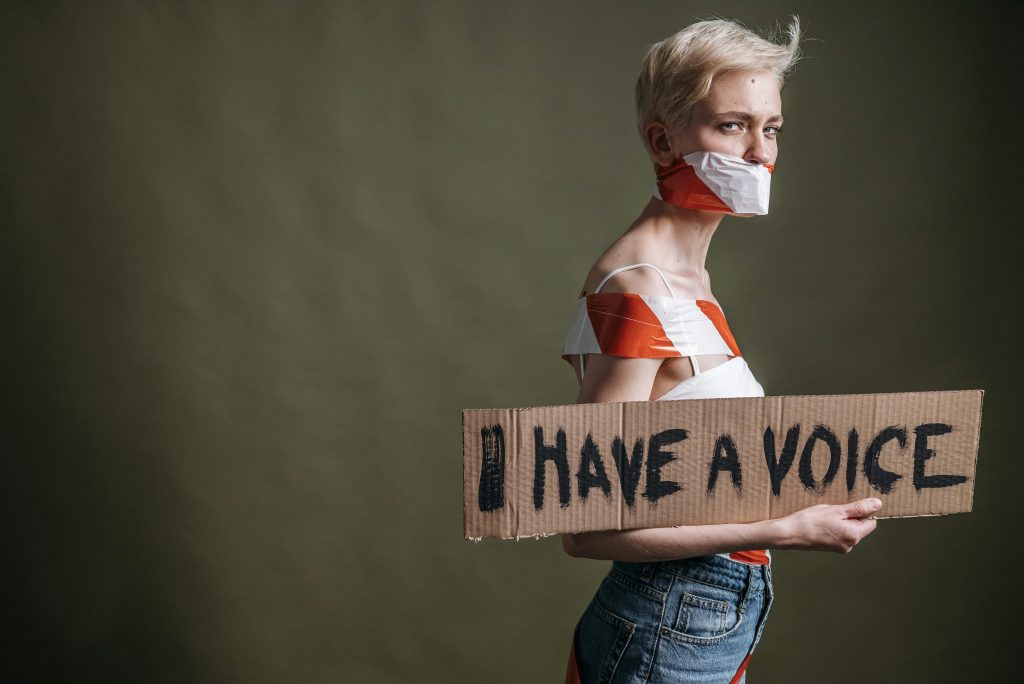
What’s the most shocking blunder you’ve experienced in your technology journey?
Navigating the Tech Career: My Most Significant Mistake In the fast-paced world of technology, even the most experienced...

Version 19: The young applicant who sought guidance on internship interviews ended up signing the agreement.
Exciting News: Secured My First Internship in Cybersecurity! I’m thrilled to share some fantastic news with the community!...
Numerous Fortune 500 firms have acknowledged employing at least one North Korean IT professional, with some even confirming dozens on their team.
The Surprising Presence of North Korean IT Workers in Fortune 500 Companies In a remarkable revelation, several Fortune...

1. Discovered a live public webcam feed of a child’s room; reached out to ROGERS ISP but received no response—what are the next steps? 2. Found a publicly accessible webcam showing a child’s bedroom; contacted ROGERS for help but got ignored—how should I proceed? 3. Spotted an open webcam stream of a child’s space and alerted ROGERS ISP; their disinterest left me unsure of what to do now. 4. Came across a live webcam of a kid’s room online; after reporting it to ROGERS, they showed no concern—what actions are recommended? 5. Encountered a public webcam feed of a child’s bedroom, contacted ISP ROGERS, but they dismissed the issue—what’s the best course of action? 6. Public webcam of a child’s sleeping area detected; reported to ROGERS but received no assistance—what should I consider doing next? 7. Found a live feed of a child’s room on a public webcam; contacted ROGERS ISP, who showed indifference—what are your suggestions? 8. A children’s bedroom webcam was accessible publicly; after notifying ROGERS, they didn’t respond—what steps can I take now? 9. Came across a visible webcam stream of a kid’s private space; reported it to ROGERS ISP but they didn’t seem to care—what should I do? 10. Spotted a live kid’s bedroom webcam feed online; contacted ISP ROGERS, but they were unhelpful—what are the recommended actions? 11. Noticed a public camera showing a child’s room; after informing ROGERS ISP, they remained indifferent—what can be done now? 12. Discovered a live webcam of a child’s room available to the public; contacted ROGERS but received no support—what steps are advisable? 13. Found an open webcam stream of a minor’s bedroom; alerted ROGERS ISP but got no response—what is the best way forward? 14. Publicly accessible webcam footage of a kid’s bedroom; contacted ISP ROGERS but was ignored—what should I do next? 15. Witnessed a live feed of a child’s bedroom through a public webcam; after reaching out to ROGERS, they were dismissive—what actions can I take? 16. A children’s sleeping space was visible via a public webcam; I reported it to ROGERS ISP but faced indifference—what’s my next move? 17. Came across a webcam streaming a child’s room that’s available online; contacted ROGERS but they didn’t respond—what steps should I consider? 18. An open webcam of a young child’s bedroom was found; after contacting ROGERS, they showed no concern—what are the options? 19. Spotted a live stream of a child’s room on a public webcam; reported it to ISP ROGERS but received no help—what’s the best way forward? 20. I found a public webcam feed of a kid’s private space; reaching out to ROGERS ISP was unhelpful—what actions do you recommend?
A Call for Action: Reporting a Public Webcam Stream in a Child’s Bedroom Recently, I encountered a concerning...

Successfully achieved the Comptia Security+ certification on my initial attempt—fear not!
Overcoming Exam Anxiety: My Journey to Passing the CompTIA Security+ Certification I am thrilled to share that I...

Version 24: Feeling overwhelmed before my big interview at the company I’ve always dreamed of joining!
Embracing Nerves Before My Dream Interview: A Personal Journey Today marks a significant moment in my career journey...

Decoding the TLS Handshake: All the Steps That Secure Your Connection and Show the Padlock 🔒
Understanding the TLS Handshake: What Happens Before You Get that Secure Padlock 🔒 When you click on an...

What single question leaves North Korean counterfeit laborers completely baffled?
Title: The Challenge of Engaging with North Korean Fake Workers: A Unique Perspective In the realm of unusual...

1. Numerous Fortune 500 firms have revealed they’ve employed North Korean IT professionals, sometimes in large numbers. 2. Several global giants listed in the Fortune 500 have acknowledged onboarding North Korean tech specialists, with some hiring dozens. 3. It’s been disclosed that many top-tier Fortune 500 companies have brought on North Korean programmers, occasionally in significant quantities. 4. A surprising number of Fortune 500 corporations have admitted to employing North Korean IT personnel, with some hiring multiple individuals. 5. Many leading companies in the Fortune 500 have confessed to hiring North Korean tech workers, sometimes in the dozens. 6. Multiple Fortune 500 companies have publicly stated they’ve recruited North Korean IT experts, sometimes in large groups. 7. Some of the world’s biggest corporations listed in the Fortune 500 have admitted to hiring North Korean programmers, at times en masse. 8. A number of Fortune 500 organizations have disclosed they’ve employed North Korean IT professionals, with some hiring multiple workers. 9. It’s been confirmed that several Fortune 500 companies have brought North Korean tech talent into their ranks, sometimes in substantial numbers. 10. Many Fortune 500 firms have acknowledged the employment of North Korean IT workers, with some hiring dozens at a time. 11. The Fortune 500 list includes companies that have admitted to hiring North Korean programmers, in some cases quite a few. 12. Several top-tier corporations in the Fortune 500 have openly acknowledged employing North Korean IT specialists, including in large quantities. 13. Instances have emerged of Fortune 500 companies hiring North Korean tech employees, sometimes in the dozens. 14. It has come to light that numerous Fortune 500 companies have employed North Korean IT personnel, often in sizeable groups. 15. A number of Fortune 500 organizations have revealed their use of North Korean IT workers, with some hiring many at once. 16. Across the Fortune 500, many companies have stated they’ve hired North Korean programmers, sometimes in large numbers. 17. Several leading Fortune 500 firms have admitted to employing North Korean tech staff, with some hiring dozens of individuals. 18. The employment of North Korean IT specialists has been acknowledged by many Fortune 500 companies, sometimes in significant numbers. 19. It’s been reported that a number of Fortune 500 companies have hired North Korean programmers, occasionally in the dozens. 20. Many of the world’s top companies listed in the Fortune 500 have confessed to bringing North Korean IT workers onboard, sometimes in large groups.
The Surprising Truth: Fortune 500 Companies Employing North Korean IT Professionals In a surprising revelation, many Fortune 500...

1. Unbelievable Incident: Sex Toy Gets Hijacked by Malware! 2. You Won’t Believe This Rare Case of a Malware-Infected Sex Toy! 3. Unexpected Cyber Threat: Sexy Toy Turns Into a Malware Carrier! 4. Surprising Cybersecurity Breach Involving a Sex Toy! 5. This Unusual Scenario: Malware Infects a Personal Pleasure Device! 6. Shocking Discovery: Malware Lurks in a Sex Toy! 7. Rare Cyber Incident: Infection Spread Through a Sex Toy! 8. Out of the Ordinary: Malicious Software Attaches to a Sex Toy! 9. Unexpected Tech Threat: Malware Infection in a Sex Toy Revealed! 10. Surprising Cybersecurity Flare-Up: Sex Toy Compromised by Malware! 11. Not Your Average Tech News: Malware Infiltration of a Sex Toy! 12. Intriguing Case of a Sex Toy Contaminated by Malicious Software! 13. Cybersecurity Shock: Malware Found in a Personal Device! 14. This Isn’t Something You See Every Day: Malware Attack on a Sex Toy! 15. Unusual Malware Outbreak Linked to a Sex Toy! 16. Rare Digital Threat: Malware Infects a Sex Toy Device! 17. Cyber Threat Alert: Personal Pleasure Device Hijacked by Malware! 18. Unexpected Malware Attack: Sex Toy Becomes a Cyber Risk! 19. Curious Case of Malware Contamination in a Sex Toy! 20. Bizarre Tech Issue: Infection of a Sex Toy with Malicious Software!
Unexpected Intrusion: A Sex Toy Found with malware! In an unusual twist that blends technology and personal products,...

Attention BeyondTrust: Please refrain from contacting an employee’s supervisor when a security engineer informs you we’re not interested in your offerings.
The Importance of Professional Communication in Sales In today’s competitive business environment, maintaining professionalism while communicating with clients...