Understanding the TLS Handshake: Unveiling the Secrets Behind Your Secure Connection 🔒
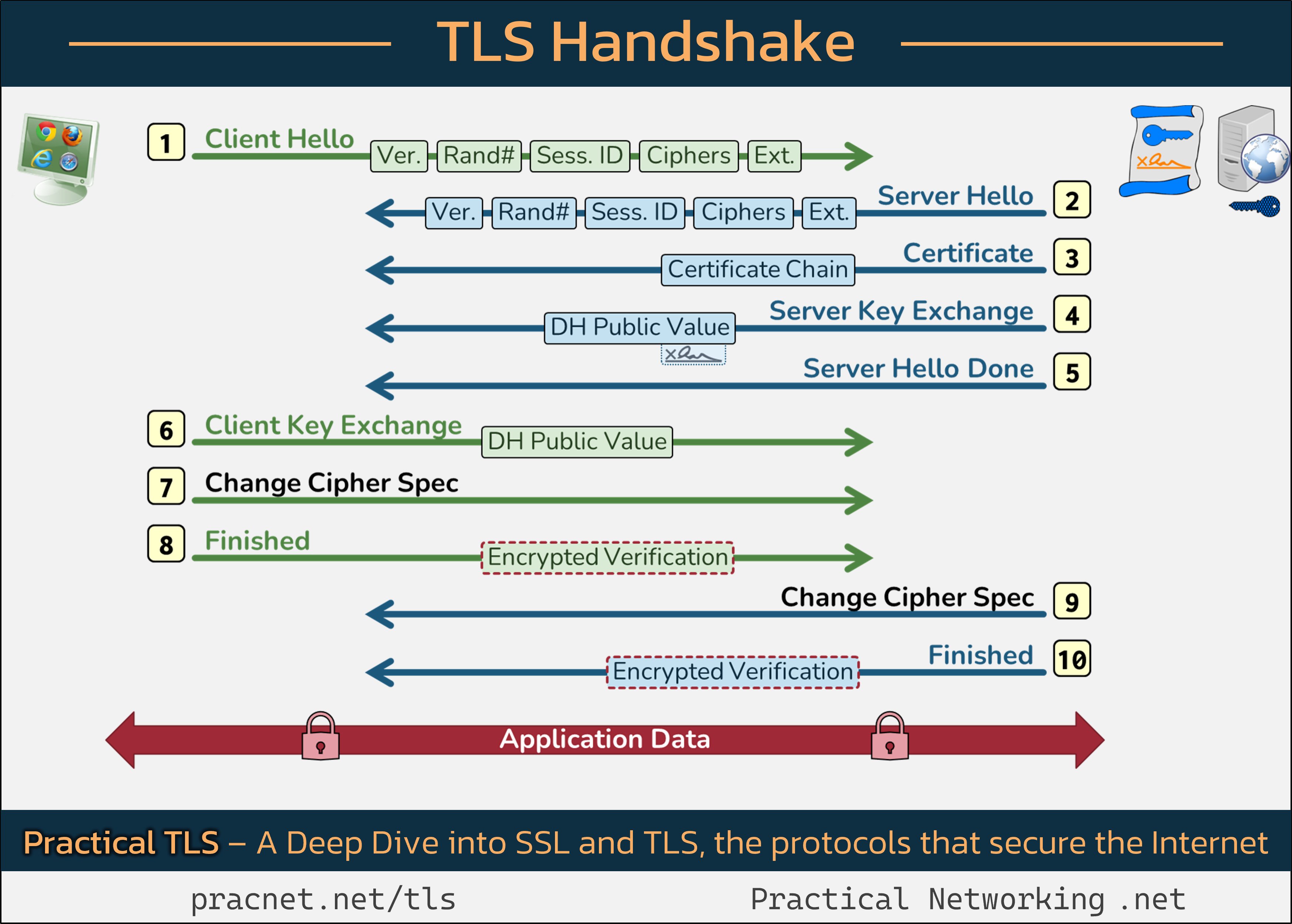
In this post, we will delve into the intricate process that occurs each time you earn the reassuring padlock symbol while browsing a secure website. This symbol, which represents a secure connection, is the result of a complex interaction between your web browser and the server hosting the website. To clarify this process, we will refer to a helpful infographic that illustrates the communication during the TLS handshake.
Introduction
Before we embark on this exploration, it’s essential to remember the primary objectives of SSL/TLS:
- ✅ Validate the server’s identity.
- ✅ Establish session keys to secure data transfers.
With this foundation laid, let’s take a closer look at the handshake process itself, broken down into its key components.
Key Concepts
Records vs. Packets: Each line in the infographic represents a “record” within the TLS handshake, which should not be confused with a packet. Records can be carried within multiple packets, and vice versa.
Cryptographic Foundations: A basic understanding of cryptographic concepts such as hashing, Message Authentication Codes (MACs), and encryption is beneficial. We won’t dive deeply into these topics here, but if you’re curious, there are many useful resources available online.
The TLS Handshake Steps
1. Client Hello
The handshake commences when the client—a.k.a. your web browser—sends a “Client Hello” message. This message contains crucial information, including:
- SSL Version: Indicates the highest SSL/TLS version supported by the client.
- Random Number: Contributes randomness to the session keys, which enhances security.
- Session ID: Used for session resumption, allowing the client and server to re-establish a previous session.
- Cipher Suites: A list of cryptographic algorithms supported by the client for authentication, key exchange, symmetric encryption, and hashing.
- Extensions: Additional features beyond the original protocol specifications.
The server will respond to the Client Hello with its own version of these fields.
2. Server Hello
The server’s response, known as “Server Hello,” includes:
- The highest SSL version supported by the server.
- Its own random number.
- A session ID
Share this content:




Thank you for sharing this detailed overview of the TLS handshake process. Understanding how secure connections are established helps in troubleshooting SSL/TLS issues effectively. If you’re experiencing problems with the padlock or secure connection indicators, here are a few tips:
If you’d like, I can assist further by reviewing your server’s SSL configuration or recommending specific settings based on your server environment. Feel free to share more details about any errors or issues you’re encountering!