
Understanding the TLS Handshake: The Steps Behind Securing the Padlock 🔒
Understanding the TLS Handshake: The Key to Secure Connections 🔒 In the world of web browsing, nothing signifies...

Is an Antivirus Unnecessary? Just Rely on Defender—Is That Enough?
Is Windows Defender Enough for Your Cybersecurity Needs? In the world of cybersecurity, the debate surrounding the effectiveness...

Device Infected: Antivirus Isn’t Providing Any Protection
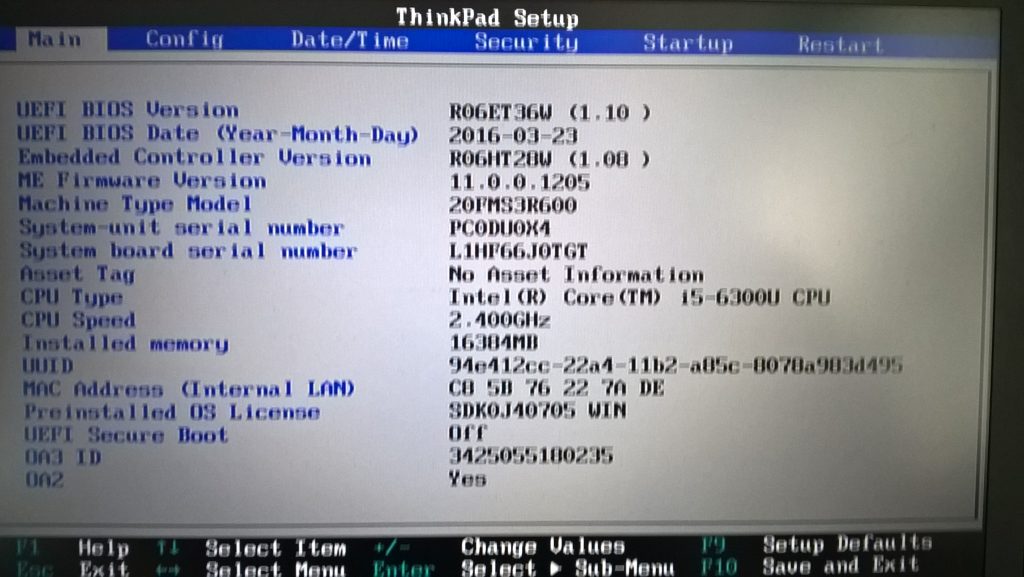
Troubleshooting a Malware Infected Device: My Personal Experience Recently, I encountered a frustrating issue with my computer after...

The device has been compromised and the antivirus software isn’t responding
Battling Malware: A Personal Encounter with an Infected Device Dealing with an infected device can be incredibly frustrating,...

Unexpected Incident: Malware Found on a Sex Toy – A Rare and Surprising Case
Unexpected Surprises: A Vibrator with Malware? In an astonishing turn of events, a sex toy has been discovered...

Discovering a “hacker” email in my spam folder claiming a countdown started when I opened it—I’m panicking!
Navigating the Fear of Cyber Extortion: A Personal Experience Recently, I stumbled upon an alarming email tucked away...

I’m Nervous Before My Interview with the Company I’ve Always Dreamed Of
Overcoming Nerves: My Journey to Interviewing at My Dream Cybersecurity Company Today, in just thirty minutes, I am...

Which Anti-virus Software Currently Holds the Title as the Most Powerful?
Discovering the Most Effective Antivirus for Heavy Malware Users In the ever-evolving landscape of cyber threats, selecting the...

A student searching for internship interview advice ultimately landed the job offer
Exciting News: I Landed My First Internship in Cybersecurity! I’m thrilled to share some fantastic news with everyone!...
Only 3% of Google’s security incidents are handled by human analysts, with 97% being automated
Rethinking Cybersecurity: How Google Automates Threat Detection In an age where cybersecurity threats loom large, Google’s innovative approach...

Feeling Overwhelmed by the Threat of Lost: A Lifetime of Anxiety Due to SGLH Ransomware
The Frightening Reality of Ransomware: A Personal Experience In an unfortunate turn of events, I’ve recently become a...

Discovered a file called “Trojan:Win32/Phonzy.C!ml” on my computer
Dealing with the ‘Trojan:Win32/Phonzy.C!ml’ Threat: A Step-by-Step Guide If you’ve recently discovered a file labeled ‘Trojan:Win32/Phonzy.C!ml’ on your...