Understanding the TLS Handshake: Behind the Scenes of Your Secure Browsing Experience
Have you ever wondered what exactly happens behind the scenes when you browse a secure website? That little padlock icon 🔒 in your browser signifies a complex series of interactions designed to keep your data safe. This post delves into the intricacies of the TLS Handshake, exploring every step that secures your communications with a website.
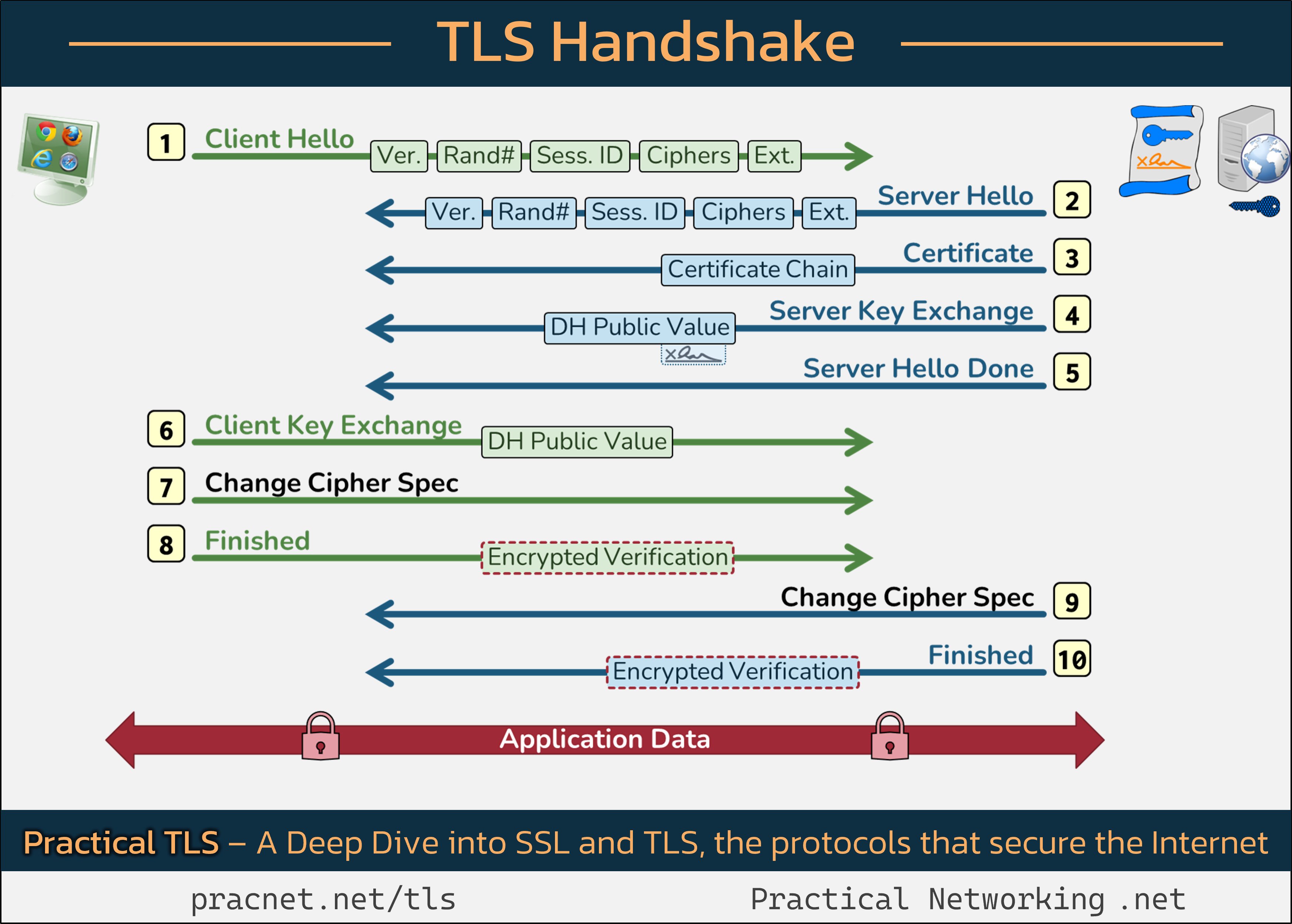
To enhance your understanding, we recommend referring to a helpful infographic that illustrates the various messages exchanged between your web browser (the Client) and the website (the Server) during a TLS session. For best results, keep this image handy as you read through the explanations below.
Introduction to TLS and SSL
Before diving into the handshake process, it’s essential to understand the primary objectives of SSL/TLS:
- Authentication: Ensuring that the Server is legitimate.
- Data Security: Establishing session keys that protect all data transferred during the session.
Let’s briefly address two foundational concepts before unpacking the TLS Handshake:
Clarifying Records and Packets
Each line depicted in the referenced image represents a “Record” transmitted during the TLS handshake, which should not be confused with a Packet. Multiple Records can be contained within a single Packet, or a single Record can extend across several Packets.
Essential Cryptographic Concepts
Understanding the TLS Handshake requires familiarity with certain cryptographic principles, including:
- Hashing
- MACs and HMACs
- Encryption
While we won’t explore these topics in detail here, you may want to review some educational videos linked above if you need more clarity.
With that foundation in place, let’s break down the components of the TLS Handshake.
1. Client Hello
The TLS Handshake begins with the Client sending a Client Hello message. This message encompasses five critical fields:
- SSL Version
- Random Number
- Session ID
- Cipher Suites
- Extensions
Each of these elements plays a role in achieving the handshake’s security objectives.
1.1 SSL Version
The Client transmits the highest version of SSL it supports (e.g., SSL 3.0, TLS 1.0, etc.). The Server reciprocates,
Share this content: