Understanding the TLS Handshake: How Your Browsing is Secured
When you visit a website that features that reassuring padlock icon, it signifies that your connection is secured through the TLS (Transport Layer Security) protocol. But what occurs behind the scenes to achieve this security? In this article, we’ll take a deep dive into the mechanisms of the TLS handshake, which establishes a secure communication channel between your browser and the server.
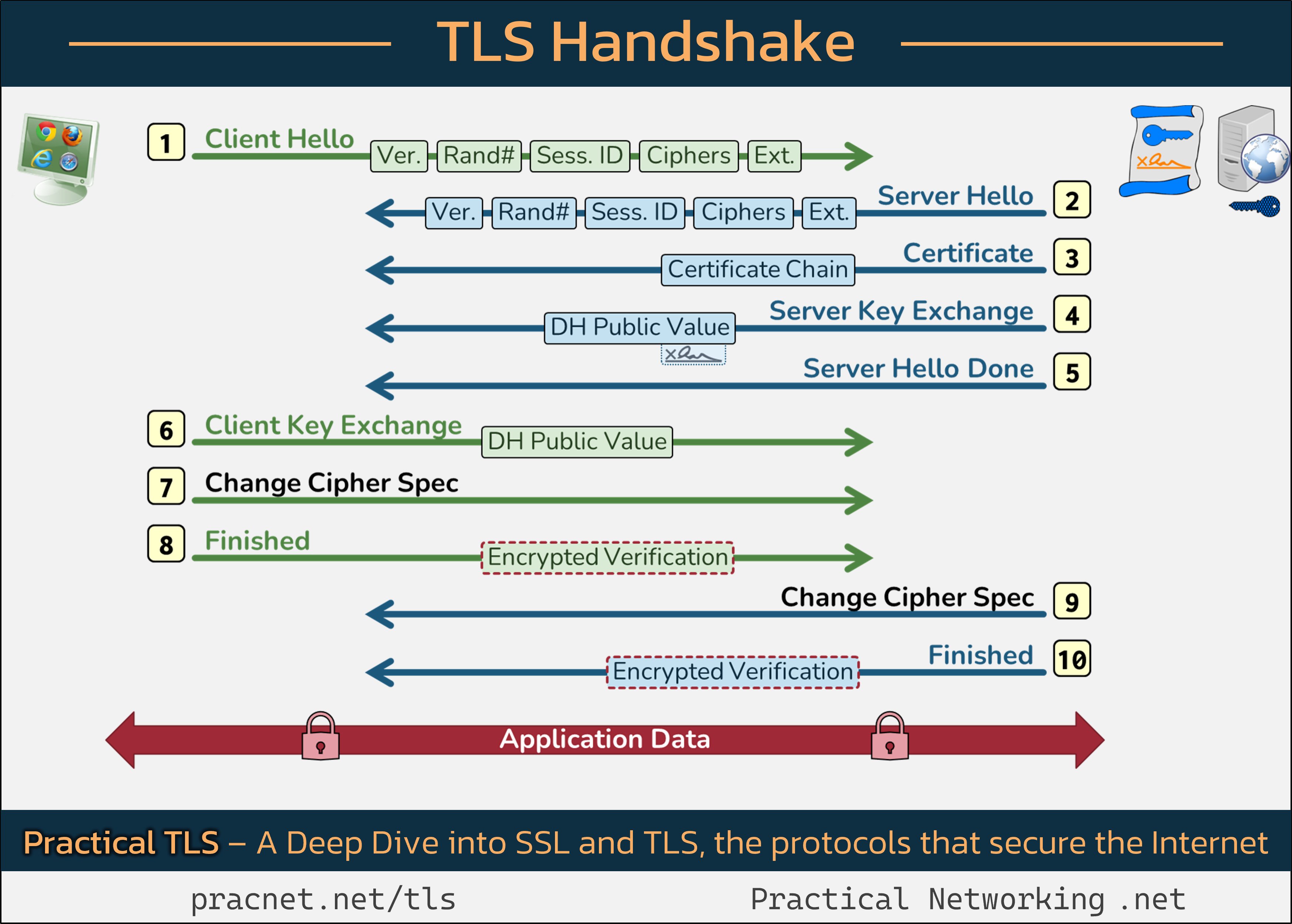
To visualize the process, feel free to open this infographic in another tab as we walk through the key steps involved in the handshake:
The Purpose of TLS
Before we navigate the handshake, it’s essential to understand two primary objectives of TLS:
- ✅ Authenticating the server’s identity
- ✅ Establishing session keys to secure the transfer of data
Key Terminology
In this discussion, keep in mind that a “Record” is different from a “Packet.” Each visual representation in the infographic depicts a Record; multiple Records may reside within a single Packet or vice versa.
Additionally, familiarity with certain cryptographic concepts such as Hashing, MACs, and HMACs will enhance your understanding of the handshake process.
Step 1: Client Hello
The TLS handshake kicks off when your browser (the Client) sends a “Client Hello” message. This message contains five crucial fields:
- SSL Version
- Random Number
- Session ID
- Cipher Suites
- Extensions
Breakdown of the Client Hello Fields
-
SSL Version: Your browser indicates the highest version of SSL/TLS it supports (e.g., TLS 1.2 or TLS 1.3). The server will respond with its highest compatible version.
-
Random Number: The Client generates a 32-byte random number, contributing to the entropy necessary for creating secure session keys.
-
Session ID: This allows for session resumption, where an older session can be resumed without going through the entire handshake. For our purposes, we’ll describe a full handshake.
-
Cipher Suites:
Share this content:




Thank you for sharing this detailed overview of the TLS handshake process. Understanding the steps involved in establishing a secure connection is crucial for maintaining network security and troubleshooting SSL/TLS related issues. If you’re experiencing problems with SSL certificates or handshake failures, here are some tips:
If you’re implementing TLS on your website or server, always keep security best practices in mind, including using strong cipher suites, enabling OCSP stapling, and ensuring your certificates are renewed before expiration