Understanding the TLS Handshake: How Your Browser Secures Connections 🔒
In this post, we will explore the intricate process that occurs during a TLS handshake, which is essential for establishing secure connections between your web browser and a website. This process is crucial for obtaining that reassuring padlock symbol in your browser’s address bar.
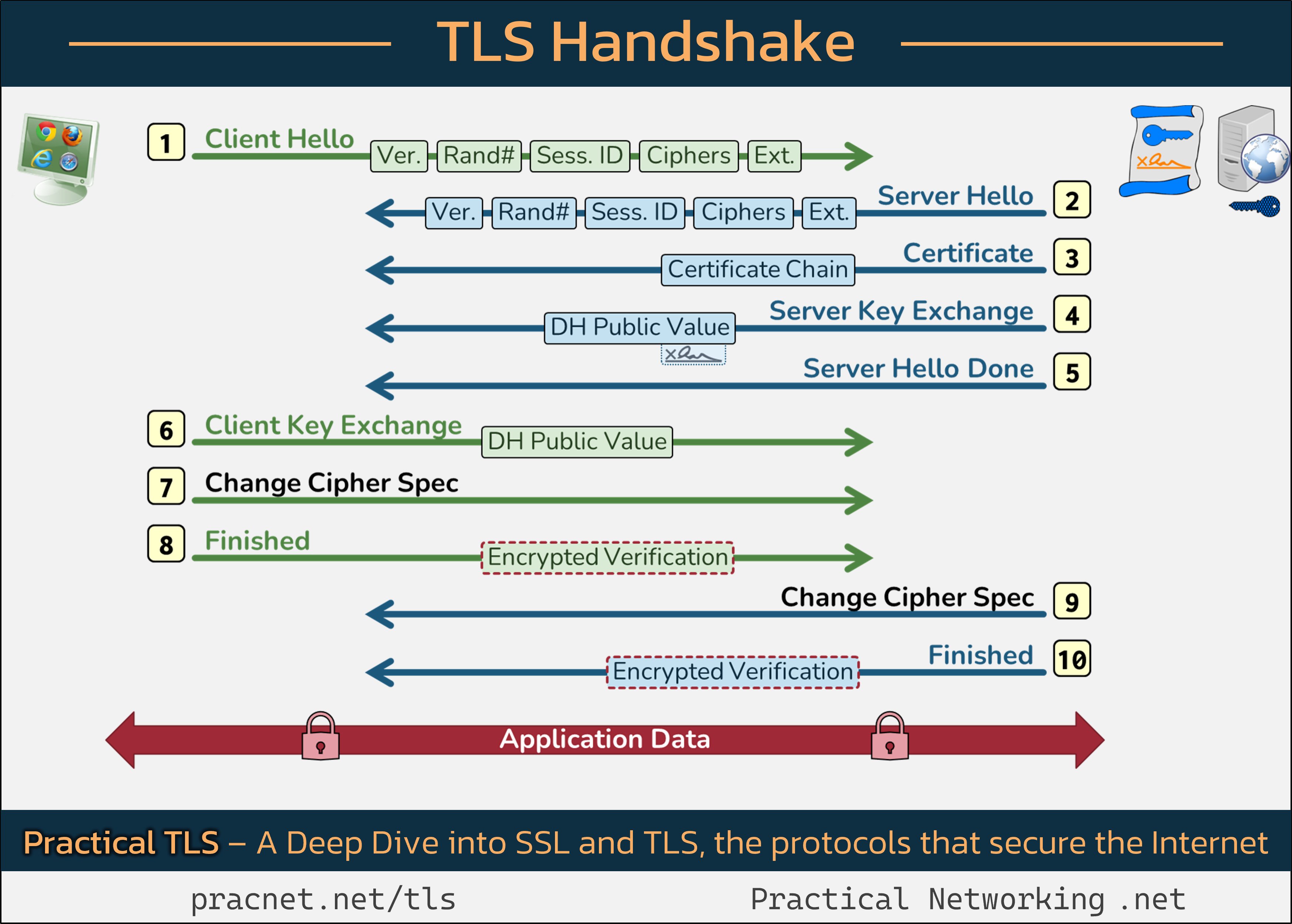
For a visual aid, you may want to keep this infographic handy as we delve into the details:
What is the Purpose of TLS?
The primary objectives of SSL/TLS are twofold:
1. ✅ To verify the server’s authenticity.
2. ✅ To create session keys that safeguard the data exchanges that follow.
Before we break down the TLS handshake, let’s clarify two fundamental concepts:
Records vs. Packets
Each line in the infographic represents a record sent during the TLS handshake. Importantly, records are not synonymous with packets; a single packet may contain multiple records, or several packets may be required to transmit a single record.
Basic Cryptography Concepts
To grasp the details of the TLS handshake, it’s beneficial to familiarize yourself with some cryptographic principles:
– Hashing
– Message Authentication Codes (MACs) and HMACs
– Encryption
We won’t delve deeply into these topics here, allowing us to focus squarely on the handshake process itself.
1️⃣ Client Hello
The handshake begins with the Client (your web browser) sending a Client Hello message, which contains five essential fields:
– SSL Version
– Random Number
– Session ID
– Cipher Suites
– Extensions
Each of these components plays a vital role in the handshake process.
1.1 SSL Version
The Client submits the highest version of SSL/TLS it supports (e.g., SSL 3.0, TLS 1.2). Subsequently, the server will reciprocate with the highest common version they both support. Presently, only TLS 1.2 and 1.3 are deemed secure.
1.2 Random Number
The Client generates and
Share this content:




Support Tips for TLS Handshake Issues
If you’re encountering problems during the TLS handshake, here are some steps you can take:
SSLProtocoldirective, and in Nginx, check thessl_protocolssetting.